Cyber Briefing: 2025.06.03
Fake Chrome extension hijacks Facebook, Chrome zero-day patched, JINX-0132 hits DevOps, White House phone hack, Cartier & North Face breached, CISA budget cut, AU enforces ransom reports.
👉 What's the latest in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Fake FB Ban Fix Extension Steals Accounts
A new scam promoted via YouTube videos is targeting Facebook users who want to recover banned pages by urging them to download a deceptive Chrome extension. Distributed from Google Drive instead of the official Chrome Web Store, this extension requests extensive dangerous permissions to access all Browse activity and cookies. The malware's core function is to silently gather all Facebook session cookies and transmit them to an attacker-controlled server, allowing account hijacking without credentials and bypassing 2FA. This tactic gives attackers full account control for potential identity theft or spreading more scams, highlighting the risk of unofficial tools and the need for user vigilance.
2. Actively Exploited Chrome V8 Flaw Patched
Google released an emergency out-of-band security update on Monday for its Chrome browser to address CVE-2025-5419, a high-severity, actively exploited zero-day vulnerability. This flaw, an out-of-bounds read and write weakness in Chrome's V8 JavaScript engine, could allow remote attackers to exploit heap corruption via crafted HTML pages. Discovered by Google's Threat Analysis Group on May 27th, the issue was initially mitigated by a configuration change the next day, with browser version 137.0.7151.68 now rolling out. This marks the third Chrome zero-day vulnerability Google has patched since the start of 2025, and users are strongly advised to update their browsers immediately.
3. DevOps Servers Hit By JINX0132 Crypto Mine
A new cryptojacking campaign, tracked as JINX-0132 by Wiz, is targeting publicly accessible DevOps web servers like Docker, Gitea, HashiCorp Consul, and Nomad to illicitly mine cryptocurrencies. Attackers exploit a wide range of known misconfigurations and vulnerabilities to deliver miner payloads, often downloading necessary tools directly from public GitHub repositories to evade attribution. This campaign notably marks the first publicly documented instance of Nomad misconfigurations being exploited in the wild, with some compromised instances managing hundreds of resource-rich clients.
For more alerts, click here!
💥 Cyber Incidents
4. White House Chief of Staff's Phone Hacked
The White House is investigating a security incident where unknown individuals accessed contacts from the personal phone of chief of staff Susie Wiles and used them to impersonate her with other top officials. Attackers reportedly used AI to mimic Wiles' voice in calls and sent texts from an unknown number, sometimes asking recipients to switch to platforms like Telegram. This is the second known targeting of Wiles, following a 2024 attempt on her email, and the latest cybersecurity issue for the Trump administration, which has prompted an FBI probe.
5. Cartier Data Breach Exposes Client Info
Luxury brand Cartier has warned customers of a data breach where an unauthorized party gained temporary access to its systems and stole limited client information, including names, email addresses, and countries of residence. While emphasizing that sensitive financial details like passwords or credit card numbers were not compromised, Cartier advised affected clients to remain vigilant for unsolicited or suspicious communications due to the nature of the exposed data. The company has contained the issue, informed relevant authorities, and is working with external cybersecurity specialists to investigate and strengthen its security posture, though it hasn't disclosed the number of people affected or when the breach occurred.
6. The North Face Hit By 4th Credential Hack
Outdoor apparel retailer The North Face is notifying customers that their personal information, including names, purchase history, and contact details, was stolen in an April 2025 credential stuffing attack on its website. While payment information was not exposed, this marks the fourth such incident for the brand since 2020, attributed to reused passwords and a lack of enforced multi-factor authentication. This follows a March 2025 credential stuffing attack on parent company VF Outdoor that also impacted The North Face accounts. The company discovered the latest breach on April 23rd and stated an attacker launched a small-scale attack, though the exact number of newly affected customers was not specified in the recent notice.
For more incidents, click here!
📢 Cyber News
7. New CISA Budget Slashes Staff And Funds
A Trump administration budget plan for fiscal year 2026 proposes a roughly 17% spending cut for the U.S. Cybersecurity and Infrastructure Security Agency (CISA), eliminating over a third of its staff and key outreach programs. This plan would reduce CISA's cyber operations by nearly $150 million, cut election security funding, and drastically slash resources for risk management, stakeholder engagement, and international coordination. While top DHS and CISA officials defended the cuts, bipartisan lawmakers and experts like Michael Daniel warned they could cripple CISA's ability to counter rising threats and reduce incident response capabilities. The proposed workforce reductions are extensive, affecting nearly every CISA division, including significant cuts to mission support, the cybersecurity division, and eliminating the Intelligence Unit entirely.
8. Aussie Ransom Reporting Rules Now In Effect
New ransomware payment reporting rules under Australia's Cyber Security Act 2024 took effect on May 30th for organizations with over AUS $3 million turnover and critical infrastructure operators. These entities must now report any ransomware payments to the Australian Signals Directorate within 72 hours, including payment details and attacker communications, or face civil penalties, though public sector bodies are exempt. Australia is the first country with such mandatory reporting, aimed at increasing visibility into attacks to help combat cybercriminals and potentially deter victims from paying ransoms. The Act also introduces new security standards for smart device manufacturers effective in 2026 and will establish a Cyber Incident Review Board for significant incidents.
9. Microsoft and CrowdStrike Align Hacker Names
Microsoft and CrowdStrike have partnered to align their distinct threat actor taxonomies, publishing a new joint mapping to help security professionals connect insights faster and reduce confusion caused by different vendor naming conventions. This initiative, which does not aim to create a single naming standard, has already deconflicted over 80 adversaries and will see contributions from Google/Mandiant and Palo Alto Networks Unit 42. CrowdStrike likens the new glossary to a "Rosetta Stone," enabling better correlation of threat actor aliases and extending attribution across more vectors for a richer view of adversary campaigns. The ultimate goal is to make tracking overlapping threat actor activity easier and build a more accurate, community-driven view of malicious campaigns to help defenders respond more effectively.
For more news, click here!
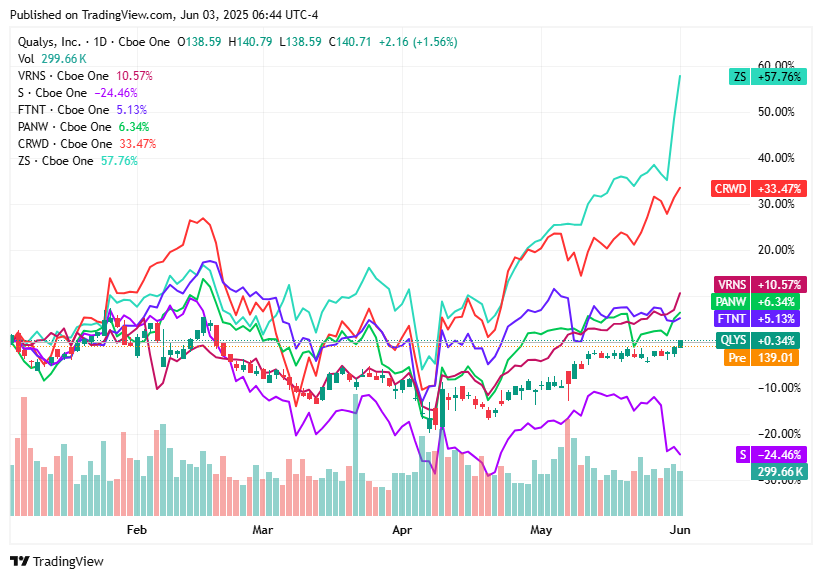
📈Cyber Stocks
As the U.S. stock market opens on Tuesday, June 3, 2025, here’s how top cybersecurity stocks are performing, reflecting strong earnings, AI partnerships, and bullish investor sentiment:
Zscaler: Stock up after strong Q3 and new AI deal with Vectra; now at $295, up 60% YTD.
Varonis: Trading near $49, with rising momentum and improving strength rating.
Palo Alto: Shares up 23% in a month, hitting $196 after strong earnings and bullish analyst outlook.
Qualys: At $142, shows bullish double-bottom pattern; strength rating climbs to 72.
CrowdStrike: Recovered to $480 after July 2024 bug; strong fundamentals, up 40% since.
Fortinet: At $102, boosted by 13% revenue growth and $1B stock buyback expansion.
💡 Cyber Tip
Do not install Chrome extensions from Google Drive or unofficial sources.
Scammers are spreading fake Chrome extensions through YouTube videos, claiming they can help you recover banned Facebook pages. Instead, these extensions steal your Facebook session cookies and give attackers full access to your account, even without your password or two-factor authentication.
✅ What you should do
Only install Chrome extensions from the official Chrome Web Store.
Never trust download links shared in YouTube videos or social media posts claiming to fix banned accounts.
Make sure to see what permissions an extension wants before installing it. Avoid ones that ask for full access to your activity or data.
Log out of Facebook if you suspect your session was hijacked and change your password immediately.
Enable login alerts and monitor your account activity for suspicious access.
✅ Why this matters
This scam gives hackers full control of your Facebook account and can lead to identity theft or further scams using your profile. Staying cautious with browser extensions is key to protecting your online identity.
📚 Cyber Book
Social Media & Cyber Security: Protecting Your Online Presence in the Digital Age by Dr. Simohamed Roudani
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.