Cyber Briefing: 2025.06.02
Linux bugs leak password hashes, GitHub flaws spread via AI, and Google Script hosts phishing. Hospitals, Moscow, and Puerto Rico hit. CSRB urged back, malware tools seized, Conti boss named.
👉 What's the latest in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Linux Core Dump Flaws Risk Password Leaks
The Qualys Threat Research Unit has discovered two critical race condition vulnerabilities, CVE-2025-5054 and CVE-2025-4598, in Linux core dump handlers apport and systemd-coredump. Affecting major distributions like Ubuntu, RHEL, and Fedora, these flaws could allow local attackers to access sensitive data, including password hashes, by manipulating SUID program core dumps. While exploit complexity varies and vendors have issued advisories, Qualys demonstrated proof-of-concept attacks that successfully extracted /etc/shadow content.
2. GitHub Code Flaw Replicated By AI Models
A new research study has identified a widespread path traversal vulnerability in a common Node.js code pattern, affecting 1,756 open-source GitHub projects, many with critical CVSS scores. This flaw, which allows attackers to access files outside restricted directories, propagated through developer resources like Stack Overflow and GitHub Gist due to misconceptions about its security despite occasional concerns. Alarmingly, the study also found that this vulnerable code pattern has "poisoned" large language models, with 95% of tested LLM-generated code samples for static file servers containing the same flaw.
3. Google Script Used In New Phishing Scams
The Cofense Phishing Defense Center has uncovered a strategic phishing campaign where attackers leverage Google Apps Script, a legitimate platform, to host deceptive phishing pages. Masquerading as urgent invoice emails from spoofed domains, these attacks trick recipients into clicking links leading to fake login portals hosted on Google's trusted script.google.com domain. This method exploits users' inherent trust in Google's environment to harvest sensitive credentials, which are then captured via a PHP script and sent to the attackers.
For more alerts, click here!
💥 Cyber Incidents
4. Covenant Health Cyberattack Shuts Hospitals
A cyberattack has impacted three Covenant Health hospitals in New England, forcing them to shut down all data systems to contain the incident, which began around May 26th, 2025. The affected facilities include St. Joseph Hospital and St. Mary’s Health System in Maine, and St. Joseph Hospital in New Hampshire, all part of the Catholic healthcare organization. While patient care is continuing with advisories to keep appointments, the attack has caused disruptions to phones, documentation systems, and outpatient lab services, leading to longer wait times and procedural adjustments.
5. Moscow DDoS Attack Cuts Internet For Days
A significant DDoS attack targeting Russian internet provider ASVT caused widespread internet outages for tens of thousands of people in Moscow and nearby areas for several days, starting last Tuesday. The attack disrupted ASVT's mobile app, website, and customer accounts, preventing residents in large complexes from working remotely, making card payments, and accessing buildings due to disabled internet-based intercoms. ASVT attributed the attack to the Ukrainian "IT Army," a pro-Kyiv hacker collective, although the group has not claimed responsibility for this specific incident, and is working with Russian state agencies to restore services.
6. Puerto Rico’s Justice Department Cyberattack
Puerto Rico's Justice Department is managing a cyberattack on its Criminal Justice Information System, forcing temporary service suspensions. Officials activated protocols immediately and will restore systems only when security and data integrity are fully certified and guaranteed. While details are limited, the Department reaffirmed its commitment to transparency and protecting public data, promising updates when appropriate.
For more incidents, click here!
📢 Cyber News
7. Senators Urge CSRB Return For Salt Typhoon
Several Senate Democrats have urged Homeland Security Secretary Kristi Noem to reestablish the Cyber Safety Review Board (CSRB), which the Trump administration disbanded earlier this year. The senators argue the CSRB's dismissal during its investigation into the China-linked Salt Typhoon telecom hacks deprives the public of a full understanding of these major U.S. compromises. Despite the administration's rationale of eliminating resource misuse, the senators contend that disbanding the CSRB undermines national cyber defense preparations and contradicts the stated need for external expertise.
8. Authorities Takedown Malware Hiding Tools
A multinational law enforcement operation has dismantled an online cybercrime syndicate that provided services for making malicious software undetectable by security programs. The U.S. Department of Justice, with international partners including Dutch and Finnish authorities, seized four domains like AvCheck[.]net on May 27th as part of Operation Endgame. These seized platforms offered crypting and counter-antivirus tools which allowed criminals to obfuscate malware effectively, enabling unauthorized system access. This takedown, which follows other recent disruptions like Lumma Stealer, aims to counter the threat of malware refinement, as seen with tools like PureCrypter which also aid in malware evasion.
9. Alleged Conti and Trickbot Leader Unmasked
German authorities (BKA) have identified "Stern," the suspected leader of the Trickbot and Conti cybercrime gangs, as 36-year-old Russian national Vitaly Nikolaevich Kovalev, who is now also wanted in Germany via an Interpol red notice. This identification follows previous U.S. sanctions and charges against Kovalev in February 2023 for his links to these groups, where he was known by aliases like "Bentley" and "Ben." Massive data troves from "TrickLeaks" and "ContiLeaks" exposed internal conversations and personal information, revealing Kovalev (as "Stern") was in charge of TrickBot operations and the Ryuk and Conti ransomware gangs, approving attacks and even legal support for arrested members.
For more news, click here!
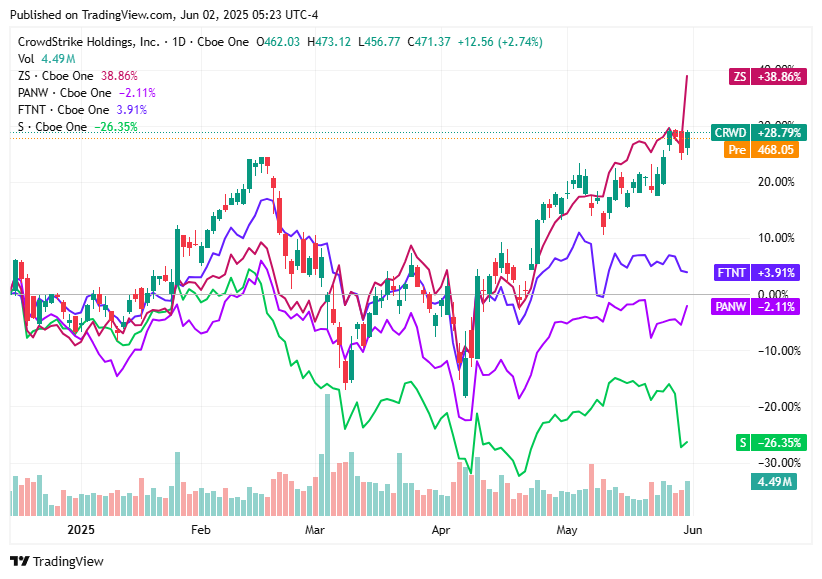
📈Cyber Stocks
On Friday, May 30, 2025, Zscaler rose 9.79%, CrowdStrike Holdings gained 2.74%, Palo Alto Networks increased 3.55%, Fortinet dipped 0.25%, and SentinelOne edged up 1.27%.
💡 Cyber Tip
Just because a link comes from Google doesn't mean it's safe.
Cybercriminals are using Google’s legitimate Apps Script platform to host fake login pages and steal your credentials. These phishing emails look like urgent invoices and lead to trusted “google.com” links, making them seem real.
✅ What you should do
Always double-check invoice emails before clicking links. Verify the sender’s email address and contact the company directly if you are unsure.
Be cautious of emails that create urgency or ask you to log in quickly
Look closely at login pages. Even small differences could mean it’s a fake.
Never trust a website just because it’s hosted on a google.com subdomain.
Use multi-factor authentication on your accounts to protect against credential theft.
✅ Why this matters
These scams are dangerous because they use trusted Google links to fool you into giving away your passwords. One click could compromise your email, files, or sensitive business information.
📚 Cyber Book
How to Land Your First Cybersecurity Job: A Step-by-Step Guide to Launching Your Career in Cybersecurity by Yehyun Park
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.