Cyber Briefing: 2025.05.27
Luna Moth hits law firms, Winos4.0 spreads via fake apps, and GhostSpy targets Android. Data breaches hit Adidas, Coke, and AXT. Banks fight SEC rule, while Microsoft and AMD back global cyber growth.
👉 What's the latest in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. FBI Warns Luna Moth Targets US Law Firms
The FBI warned that the Luna Moth extortion group has targeted U.S. law firms for two years. They use callback phishing and spoofed IT support calls to socially engineer employees for remote access. After gaining access via tools like Quick Assist attackers exfiltrate data using Rclone or WinSCP. Luna Moth then demands ransoms not to leak stolen data with the FBI urging improved defenses.
2. Winos 4.0 Malware Spread Via Fake Installers
A malware campaign uses fake software installers like LetsVPN to deliver the Winos 4.0 framework. This is done via Catena, a memory-resident loader that evades antivirus targeting Chinese-speaking users. Winos 4.0 an advanced C++ framework based on Gh0st RAT harvests data and offers remote shell. The campaign shows tactical shifts using NSIS installers reflective DLL injection and Defender exclusions.
3. GhostSpy Android Malware Full Device Control
New Android malware GhostSpy gives attackers full device control using advanced surveillance and evasion techniques. It infects by exploiting Accessibility Services to silently install payloads and gain extensive permissions. GhostSpy steals data like credentials, 2FA codes and files while using anti uninstall and C2 communication. Security experts recommend robust defenses, user education and monitoring to counter this pervasive threat.
For more alerts, click here!
💥 Cyber Incidents
4. Adidas Data Breach Exposes Customer Contacts
German sportswear giant Adidas recently disclosed a new significant data security breach event. Attackers successfully hacked a third-party customer service provider utilized by the major brand. This unfortunate breach resulted in some Adidas customers' personal data being stolen. Adidas stated it recently became aware of this new concerning security incident. An unauthorized external party had obtained access to certain sensitive consumer data files. The company immediately took swift steps to fully contain the ongoing security incident.
5. Everest Ransomware Leaks Coke Staff Data
The Everest ransomware group leaked Coca-Cola Middle East employee data online after an attack. This 502MB data dump includes 1104 files with names, addresses, passports, banking and HR details. Exposure of such sensitive personal and internal administrative information creates significant cybersecurity risks. It is currently unknown if Coca-Cola negotiated or paid a ransom to the Everest group.
6. Semiconductor Firm AXT Hit by Data Breach
California semiconductor firm AXT Inc. reported a data breach after detecting network compromise in April 2025. An investigation confirmed unauthorized third party access to sensitive personal information in its systems. AXT began notifying affected individuals on May 20 offering credit monitoring and specific data details. The company founded 1986 makes semiconductor substrates and employs over 1000 people globally.
For more incidents, click here!
📢 Cyber News
7. Banking Groups Urge SEC To Repeal Cyber Rule
Five top U.S. banking associations are petitioning the SEC to repeal its cyber incident disclosure rule. They argue the four-day public reporting mandate harms firms misleads investors and aids threat actors. The groups also state this rule conflicts with national security efforts and can hinder investigations. Urging full rescission they say existing rules suffice and SEC guidance shows the current rule's flaws.
8. Microsoft ARC Initiative Boosts Africa
Microsoft launched its Advancing Regional Cybersecurity Initiative to boost cyber resilience globally. It kicks off in Africa with Kenya's NC4 focusing on cooperation threat intelligence and capacity building. This Kenyan partnership will develop a shareable planning toolkit through roundtables and crisis simulations. Microsoft envisions this as a repeatable model for the Global South building on its Accra Call commitments.
9. Red Hat And AMD Partner For Advanced AI GPUs
Red Hat and AMD announced a strategic collaboration to advance artificial intelligence workload management. This partnership integrates AMD Instinct GPU Operators into Red Hat OpenShift AI for enhanced processing power. It aims to streamline AI adoption for enterprises in hybrid cloud environments using validated tooling. Both companies highlight open collaboration to democratize access to AI technologies for developers and organizations.
For more news, click here!
📈Cyber Stocks
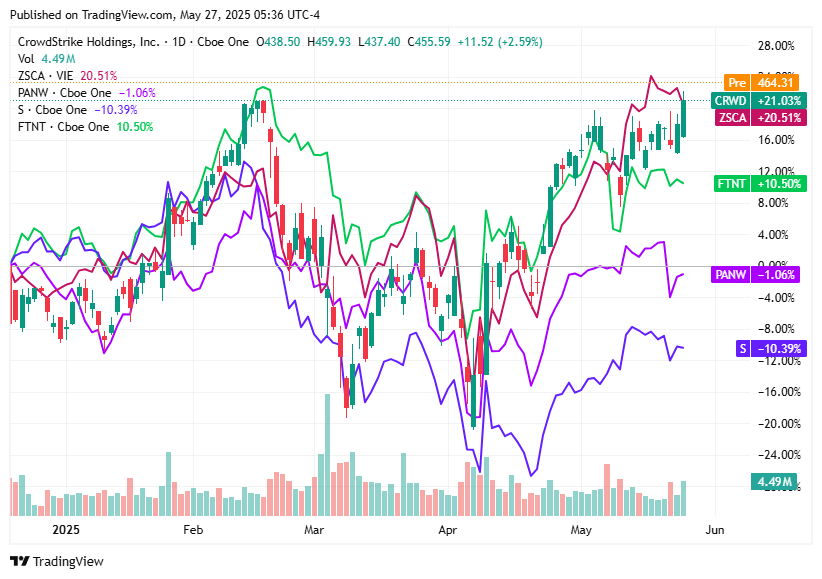
On May 26, 2025, Zscaler rose 0.57%, CrowdStrike Holdings gained 2.61%, Palo Alto Networks increased 0.36%, Fortinet dipped 0.46%, and SentinelOne declined 0.15%.
💡 Cyber Tip
Be careful with unexpected calls or emails claiming to be from IT support.
The FBI warns that a cybercriminal group called Luna Moth is targeting U.S. law firms and other businesses using fake IT support calls and phishing emails. Their goal is to trick employees into granting remote access so they can steal sensitive information and demand a ransom.
✅ What you should do
Do not call phone numbers listed in suspicious emails about fake subscriptions or invoices.
If someone calls claiming to be from your company’s IT team, always verify their identity through an official channel.
Never install remote access software (like Quick Assist, AnyDesk, or Zoho Assist) unless instructed directly by verified IT personnel.
Be cautious of any email or call that pressures you to act quickly or threatens consequences.
✅ Why this matters
These attacks are highly convincing and use real tools to steal company data. One wrong move can give cybercriminals full access to your device and sensitive files.
📚 Cyber Book
CYBERSECURITY: A Children's Guide to Being Safe Online by Caryn Warren
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.