Cyber Briefing: 2025.05.14
A vulnerability in Uncanny Automator, fake Solana PyPI package targets developers. Microsoft patched a critical Linux Defender bug, Alabama's cybersecurity incident. EU new vulnerability database.
Listen to our podcast here
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this?
👉 What's happening in cybersecurity today?
🚨 Cyber Alerts
1. Uncanny Automator Bug Risks WordPress Sites
A critical PHP Object Injection vulnerability was discovered in the Uncanny Automator WordPress plugin, a tool active on over 50,000 websites. This security flaw could allow authenticated attackers, even those with minimal subscriber-level access, to delete vital files like wp-config.php.
2. Devs Hit By PyPI Solana Token Secret Theft
A malicious package named "solana-token" was discovered on the Python Package Index (PyPI). Disguised as a Solana blockchain tool, it actually stole source code and developer secrets, affecting 761 downloads before removal.
3. Microsoft Defender Bug Allows SYSTEM Access
A security flaw, CVE-2025-26684, was discovered in Microsoft Defender for Endpoint on Linux systems. This vulnerability allowed authenticated local attackers to elevate their privileges to SYSTEM level, gaining complete control.
For more alerts, click here!
💥 Cyber Incidents
4. Alabama Cybersecurity Event Hits Services
Alabama is responding to a cybersecurity incident that disrupted government services and website access. Governor Kay Ivey confirmed that some employee credentials were compromised but no resident data was stolen.
5 . Andy Frain Data Breach Impacts 100k People
Andy Frain Services notified over 100,000 individuals about an October 2024 data breach that compromised personal information. The ransomware group Black Basta claimed responsibility for stealing 750 GB of data, though the company has not confirmed this.
6. Hong Kong DSC Hit By Ransomware Attack
Hong Kong's Drug Safety Testing Center, under HKSTP, experienced a malicious ransomware attack on its computer systems on May 12th. This security incident compromised data belonging to approximately 30 employees and 20 customers of the center.
For more incidents, click here!
📢 Cyber News
7. New EU Vulnerability Database Launched
The European Union has launched its new vulnerability database, the European Union Vulnerability Database (EUVD), developed by ENISA since the NIS2 Directive. This beta launch in mid-April occurred amid uncertainty about the future operation of MITRE’s CVE Program. The EUVD will provide aggregated, actionable information on ICT vulnerabilities, including their exploitation status and mitigation measures.
8. Aussie Data Breach Reports Hit 5 Year High
Australia experienced its highest number of reported data breaches this decade in late 2024, with 527 notifications. The Office of the Australian Information Commissioner (OAIC) report revealed malicious attacks like ransomware and compromised credentials drove most incidents. Health and government sectors were prime targets, alongside rising supply chain breaches and significant human error.
9. Google Hunts Malicious Linux Desktop Files
Google Threat Intelligence has launched a new blog series to share advanced threat hunting techniques with security professionals. The initial focus is on detecting malicious .desktop files on Linux systems, which attackers use to hide malicious commands. These files often employ decoy PDF documents hosted on Google Drive to distract victims while malware downloads.
For more news, click here
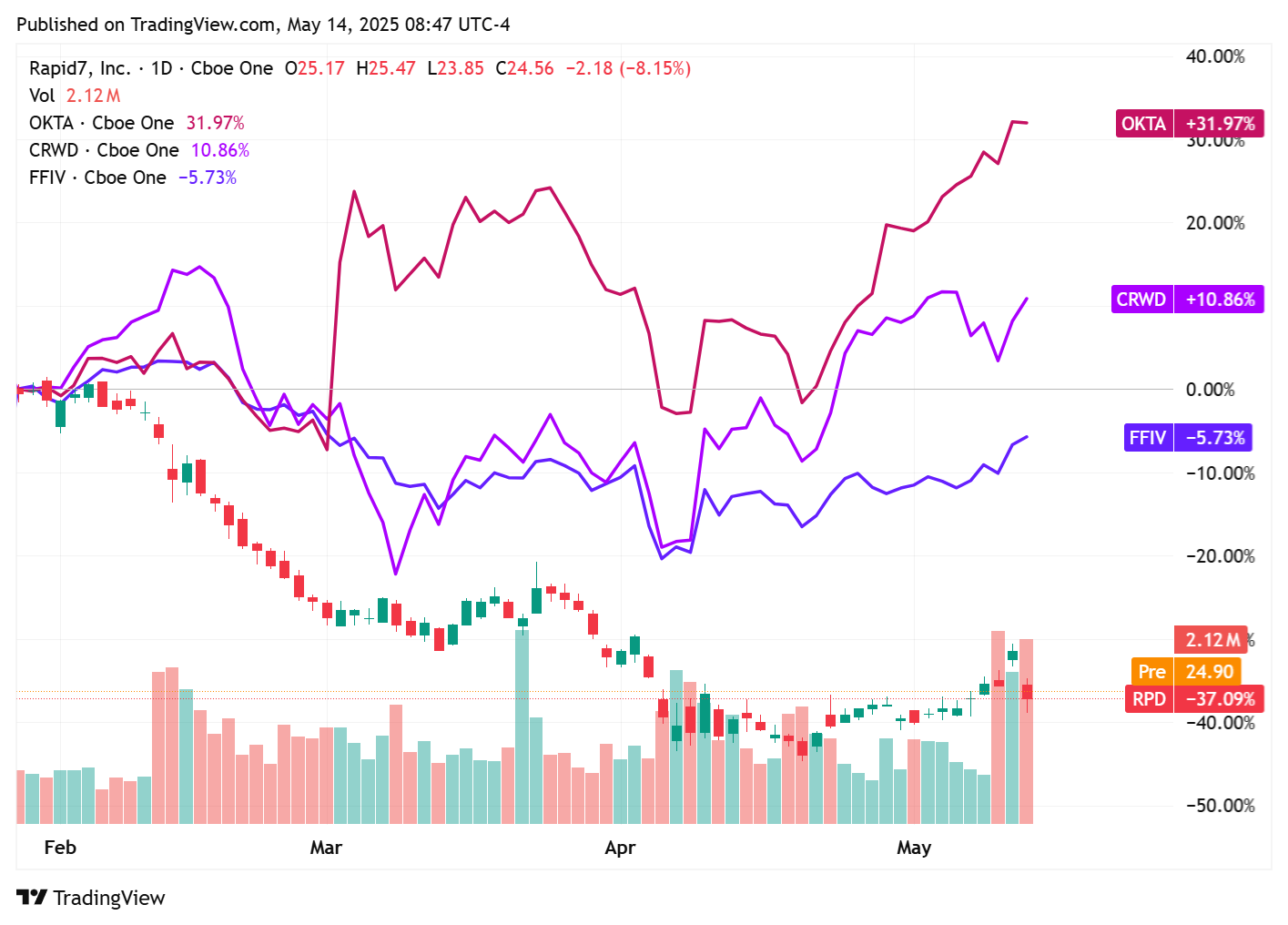
📈Cyber Stocks
💡 Cyber Tip
Update Uncanny Automator Plugin Immediately
A critical vulnerability has been discovered in the Uncanny Automator WordPress plugin, used on over 50,000 sites. This flaw could allow attackers with even the lowest level of access (like subscribers) to delete sensitive files such as wp-config.php.
Actions You Should Take:
Update the plugin immediately to the latest patched version from the WordPress plugin repository.
Check your site for unauthorized users, especially new subscribers or unusual accounts.
Review your server files (e.g., wp-config.php) for any signs of tampering or deletion.
Enable a Web Application Firewall
Back up your site regularly, especially before applying security patches.
Why it matters: Low-level user accounts can be exploited, this means even a simple subscriber could trigger the attack. If successful, attackers can delete configuration files, disabling your site or enabling further compromise.
📚 Cyber Book
Cyber Smart: Five Habits to Protect Your Family, Money, and Identity from Cyber Criminals by Bart R. McDonough
That’s a wrap on today’s threats. Stay sharp, patch often, and see you in tomorrow’s briefing.
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.